I am a Zivver admin
Configure and manage Zivver
Set admin roles
Role-Based Access Control
With Role-Based Access Control (RBAC), you can assign specific admin roles (Full admin, Policy admin, Support, and Auditor) within your Zivver organization settings, streamlining user management and enhancing security. RBAC helps to improve the efficiency of your administrative processes while safeguarding impactful functionalities & information. On this page you can read all about using RBAC in Zivver for your organization.
Role-Based Access Control is part of our Advanced Administration Bundle, containing capabilities that larger organizations require while SMBs do not. Please contact your contact person at Zivver or our support team if you are interested in this feature.
Change roles
Follow these steps to set admin roles:
- Log in to the Zivver WebApp as Full Admin.
Any existing admin before RBAC was enabled will have the Full Admin role. - Click
Organization Settings.
- Expand
User administration.
- Click Accounts.
- Click next to the account for which you want to change the role.
- Scroll down to the Account type pane.
- Select Administrator.
- Choose a role from the Administrator role dropdown menu.
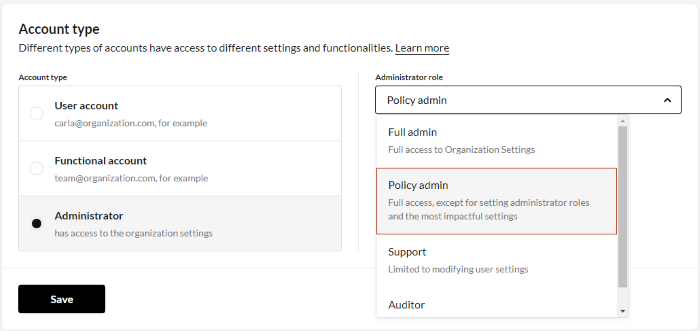
- Click .
- Review and confirm your changes.
If this account was not an administrator yet and Single Sign-On is enabled, you need to enter a temporary password for the account
Roles
With RBAC, access to the Zivver organization settings can be granted based on four common administrative roles:
- Full admin: Full edit access to all settings and the ability to manage the roles of other admins
- Policy admin: Edit access to all settings, except for the most impactful settings that only need to be configured once, plus access to audit and communication logs
- Support: Edit access to user accounts, but no access to impactful account settings or sensitive data
- Auditor: Read-only access to all settings, no ability to make changes
To perform tasks for effective Zivver administration, both Full admin and Policy admin must be able to perform actions that can grant access to other users’ message data (such as password resets or delegated access). Keep this in mind when assigning these roles.
Permission overview
In this overview, 📖 indicates View (Read-only) permission and ✏️ indicates Edit (Write) permission for a scope. If no icon is displayed, the role has no permission.
| Scope | Full admin | Policy admin | Support | Auditor |
|---|---|---|---|---|
| General | ||||
| Get started page | 📖 | 📖 | 📖 | 📖 |
| Organization account information (logo, branding, name, business holder) | ✏️ | 📖 | 📖 | 📖 |
| Data export host and username (excl. password) | 📖 | 📖 | 📖 | |
| List domains and (DNS) settings | ✏️ | 📖 | 📖 | |
| Inbound Direct Delivery settings | ✏️ | 📖 | 📖 | |
| NTA-7516 sending settings | ✏️ | 📖 | 📖 | 📖 |
| Organizational units | ✏️ | ✏️ | ✏️ | 📖 |
| Organization subscription | ✏️ | 📖 | 📖 | 📖 |
| Contact support page | 📖 | 📖 | 📖 | 📖 |
| User administration | ||||
| Account details (name, picture, language, timezone, displayed sender) | ✏️ | ✏️ | ✏️ | 📖 |
| Email aliases | ✏️ | ✏️ | 📖 | 📖 |
| Delegations | ✏️ | ✏️ | 📖 | 📖 |
| Password reset | ✏️ | ✏️ | ||
| Communication log | 📖 | 📖 | ||
| Accounts that need restoring after password reset | ✏️ | ✏️ | ✏️ | 📖 |
| Authentication factors | ✏️ | ✏️ | ✏️ | 📖 |
| Logout active sessions | ✏️ | ✏️ | ✏️ | 📖 |
| Administrator role | ✏️ | 📖 | 📖 | 📖 |
| Account type (user or functional) | ✏️ | ✏️ | 📖 | 📖 |
| Account status (active or suspended) | ✏️ | ✏️ | ✏️ | 📖 |
| Single Sign On settings | ✏️ | 📖 | 📖 | |
| Trusted networks | ✏️ | ✏️ | 📖 | |
| Automatic account deletion | ✏️ | 📖 | 📖 | |
| Insights | ||||
| Insights without personal data | 📖 | 📖 | 📖 | |
| Insights with personal data | 📖 | 📖 | ||
| Audit log | 📖 | 📖 | ||
| Policies | ||||
| Recipient verification | ✏️ | ✏️ | ✏️ | 📖 |
| Verification methods allowed | ✏️ | ✏️ | 📖 | |
| Trusted devices allowed | ✏️ | ✏️ | 📖 | |
| Outbound direct delivery | ✏️ | ✏️ | 📖 | |
| Business rules | ✏️ | ✏️ | 📖 | |
| Trusted domains | ✏️ | ✏️ | 📖 | |
| Organization revocation policy | ✏️ | ✏️ | 📖 | |
| Plugin settings | ✏️ | ✏️ | 📖 | |
| Recipient Experience | ||||
| Notification message | ✏️ | ✏️ | 📖 | |
| Introduce Zivver settings | ✏️ | ✏️ | 📖 | |
| Conversation starters | ✏️ | ✏️ | 📖 | |
| Organization displayed sender | ✏️ | ✏️ | 📖 | 📖 |
| Custom support channels | ✏️ | ✏️ | 📖 | |
| Integrations | ||||
| SMTP credentials | ✏️ | 📖 | 📖 | |
| DLP Gateway | ✏️ | ✏️ | 📖 | |
| API keys | ✏️ | 📖 | 📖 | |
| Google Workspace Key | ✏️ | 📖 | 📖 | |
| Grant users access to Chrome Extension Service Account Key | ✏️ | 📖 | 📖 | |
| Downloads page | 📖 | 📖 | 📖 | 📖 |
Frequently asked questions
Who can reset passwords or change primary emails of other admins?
For security reasons, only the Full Admin can reset the password or change the primary email address of any other admin. This restriction prevents restricted admins from accessing other admins’ accounts and performing actions that require higher privileges.Does RBAC also apply to users’ personal settings?
No, this functionality applies only to admin settings. It does not affect changes that users can make to their own personal profile settings (as shown in this screenshot).