I am a Zivver admin
Configure and manage Zivver
Business rules in Zivver
Introduction
As an organization, you want to prevent data leaks and comply with laws and regulations with minimal extra effort for your employees. With Zivver, you achieve this through business rules that ensure security measures are only applied when necessary.
This is done through recommendations and automatic actions based on the content and recipients of a message. For example:
- If a message or attachment is sensitive according to your policy, Zivver ensures it is secured with encryption and two-factor authentication (2FA).
- If there is a risk that an employee might send sensitive information to the wrong person, Zivver helps correct it before the message is sent.
- Set up business rules
- Business rules
- User experience
- Best practices for business rules
- Guarantee of privacy and security
- Disclaimer
Set up business rules
The business rules are flexible and can be adapted to your policy. You can choose from a wide range of standard rules or define your own. You can also determine what recommendations to employees will look like and which automatic actions Zivver will take.
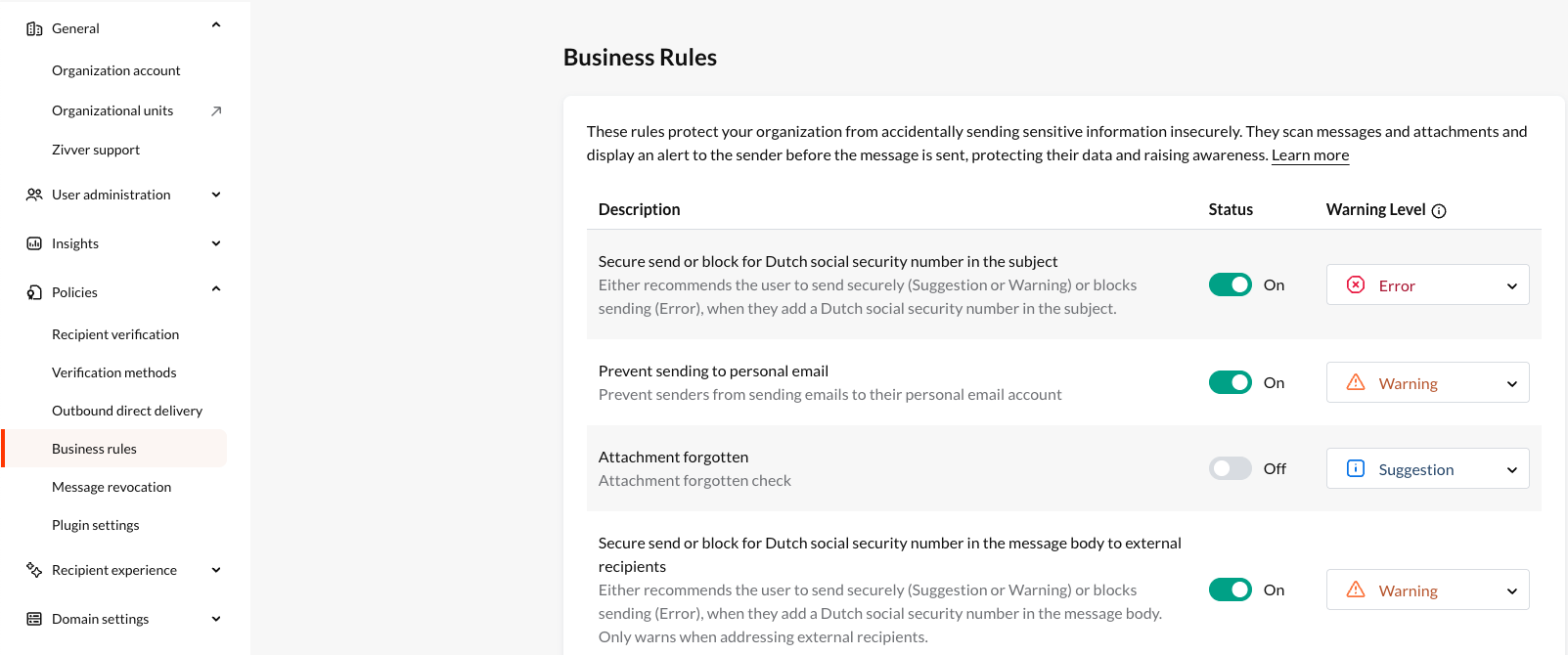
You set the business rules in collaboration with your Zivver Project Leader or Customer Success Manager. This person helps you define your secure mailing policy and translate it into the correct rules in Zivver. These will be set up in your Organization Settings under Business rules. There, you can then enable them and manage the security level for each business rule.
Below we explain which rules are available and how the security level affects the user.
Business rules
To translate your policy into business rules, it is important to know which types of rules Zivver offers. This section will help you by explaining:
- What types of business rules are available.
- What types of sensitive information each type of rule can recognize.
- How to customize your business rules to exactly fit your needs.
Types of business rules
The rules you choose determine which recommendations employees receive when they compose a message. It is important to choose rules that suit your purpose. These serve the following main objectives:
- Secure: sensitive information with encryption and two-factor authentication
- Prevent errors: Data leaks due to human error
Secure sensitive information
To prevent data breaches and comply with laws and regulations, you must secure sensitive information correctly with encryption and 2FA. However, for these measures, additional actions are necessary for both senders and recipients. Business rules ensure that these measures are only applied when the message contains sensitive information. This guarantees both security and user-friendliness.
You can identify these business rules by the name Secure sending upon [information type]. They ensure that the chosen type of information is sent securely with Zivver.

Prevent human error
While encryption and 2FA are essential, they do not protect against the main cause of data breaches: human error. With Zivver, you can help your employees avoid these mistakes.
The cause of many data leaks is sending the wrong information to the wrong person. With Zivver, you can warn employees if sensitive information is sent to an unusual recipient. You can recognize these rules by the name Check a recipient for non-recent sharing of [type of information]. They prevent sending to the wrong recipients.

In addition, many data breaches occur because too many recipients are placed in the TO and CC fields, making them visible to each other. With Zivver, you can alert your employees and encourage them to use BCC. This rule is called Consider using BCC. It prevents data leaks due to the incorrect use of BCC.

Types of sensitive information
Business rules are based on recognizing sensitive information. In this section, you can read about the types of sensitive information you can base your rules on. We distinguish between the following types:
- Clearly defined patterns, such as a social security number, a passport number, or an IBAN.
- Broad categories of sensitive information, such as medical, legal, or private.
You can base rules on both types of information. We explain each category in more detail below.
Recognize sensitive patterns with Smart Detection
An important type of sensitive information is sensitive patterns, such as social security numbers (SSNs), passport numbers, and IBAN numbers. This information is sensitive because it is used to identify individuals and can therefore be used for fraud, for example.
With the Zivver Smart Detection module, you can automatically protect and prevent human errors when sensitive patterns are present. This detection is highly precise because the patterns to detect have a clear definition.
You have access to a standard library of patterns, such as:
- Social security number
- Passport number
- IBAN
- Credit card number
- Internationally relevant patterns, such as UK NHS number and US social security number.
In addition, you can recognize organization-specific patterns, such as patient- or file numbers. These can be set to only scan in specific locations, such as the subject, body, attachment, attachment metadata, or recipient fields. You can set these up in collaboration with your Customer Success Manager.
Recognize sensitive information with Smart Classification
Although detecting sensitive patterns helps you secure a lot of sensitive information, there is still a lot of coverage missing. There is a wider range of sensitive information that does not meet a hard definition. Think, for example, of personal, medical, or legal information.
With Zivver Smart Classification, you can also recognize these types of sensitive information. This is done through a combination of detecting relevant terms and natural-language processing to determine whether the context of these terms is sensitive.
Because the definitions are less clear-cut, the risk of false reports with these rules is higher. Thus, we recommend not using more than two or three of these rules. Your Customer Success Manager can help you determine which categories are most relevant to you.
Zivver can classify the following categories of information, among others:
- Personal
- Confidential
- Employee / HR
- Financial
- Municipalities
- Legal
- Social domain
- Mental health
- Medical
- Fiscal
- Intellectual Property
- Education
Your Customer Success Manager can give you more insight into the concrete implementation of each category.
In addition to standard classifications, it is also possible to recognize sensitive information based on organization-specific terms. You can provide an Excel file with terms to your Customer Success Manager to make these rules available.
Additional settings
You have the following options to further customize the rules to your policy:
- Do not show notifications if the recipients are internal or trusted.
- Use machine learning to recognize sensitive information.
- Integration with your existing classification systems.
Do not show notifications if the recipients are internal or trusted
Many email risks apply only if the email is sent outside your organization. As a result, it is often desirable for business rules to warn only for external emails.
This is possible if you use the rules with the names that end with … to external recipients. These rules are only triggered if there is at least one external recipient. This is someone who is not part of the same Zivver organization and is not on one of the claimed domains of the organization.

Zivver recommends enabling rules only for external communication where possible. This ensures that information is secured at the right time, with minimal friction for employees.
Besides the prevention of notifications for internal recipients, your organization might also communicate with trusted partner organizations. Here you know, for example, that the partner has 2FA in place and that mail traffic goes over an encrypted connection.
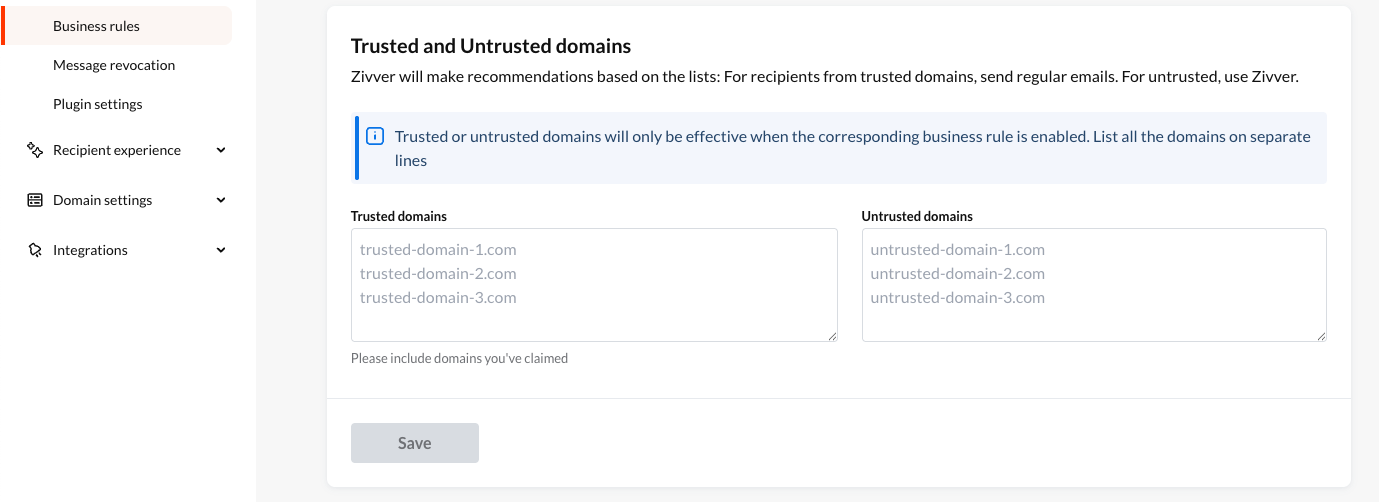
In that case, you can include these partners as trusted domains. When emails are sent to trusted recipients, you do not get notifications from business rules. The Zivver bar then indicates that all the recipients are trusted and that sending with Zivver is not necessary.
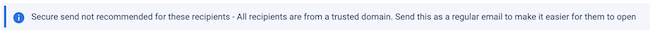
Your Customer Success Manager can advise you on how to make the best use of trusted domains. You can then manage trusted domains at the bottom of the page with business rules. If your trusted partners change, it is important to update this list as well.
Use machine learning to recognize sensitive information
As described above, sensitive information is often not unambiguously defined. For example, the presence of a few words is not enough to determine whether information is sensitive or not. Smarter methods are necessary to distinguish between, for example:
- “Will you send me the passport?” (not sensitive)
- “Attached you will find the passport” (sensitive)
Smart Classification provides a version for each relevant business rule that, in addition to detecting specific terms, also uses machine learning (artificial intelligence). This is used to determine whether the context is sensitive. Then, you get results that are three to four times more precise than a purely lexical approach.
You can recognize these rules by the fact that the name contains ‘sensitive’. For example, Secure messaging for sensitive “medical” content.
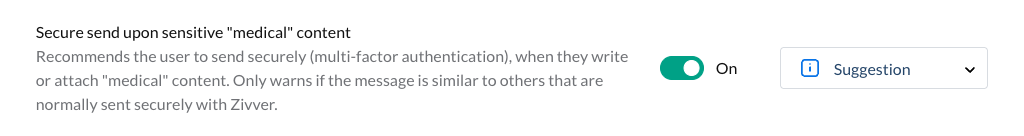
Because of its higher effectiveness, Zivver recommends that you always use this variant. The exception is if you want rules to trigger based on specific terms in a fully predictable manner.
Integration with your existing classification systems
Do you already use a system such as Microsoft Purview to classify your data? Depending on your classification system, it may be possible to link your classifications to business rules in Zivver. This would allow you to effectively extend the security policies associated with your classifications to secure mail. Ask your Customer Success Manager about the possibilities.
User experience
Business rules translate your policies into recommendations and automatic actions. You have control over how these function exactly with the security level. The security level determines how restrictive the rule is for a user. Below, you can see how a user experiences the levels Suggestion, Warning, and Error.
Suggestion A suggestion alerts employees in a non-disruptive way to the potential presence of sensitive information. They can then actively consider for themselves whether action is required. They see a blue notification and decide whether to enable secure mailing.

Warning A warning clearly alerts employees to the likely presence of sensitive information and that this requires action. How this works exactly depends on the setting of Automatically use Zivver when a business rule recommends it.
If this setting is off, employees see an orange message. They then choose whether to enable Zivver using the toggle in the bar.

If this setting is on, employees see a notification that Zivver is automatically enabled. They can still disable Zivver manually.
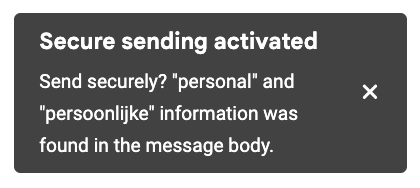
The variant where Zivver automatically goes to enabled is safer and therefore recommended. This requires that the number of rules at the Warning level is limited.
Error An error informs employees that the mail contains information that must not be sent. They see a red notification and cannot send the message until the issue is resolved.
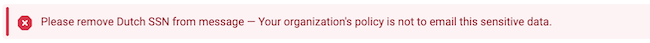
In most cases, Zivver advises against using this alert level. The reason is that it can block workflows and encourage shadow IT. Thus, use this level only for rules where you are sure the mail must not be sent. An example is if there is an SSN in the subject, because Zivver does not encrypt the subject.
Best practices for business rules
For good security, the balance between safety and user-friendliness is essential. Security measures are necessary to prevent data leaks and to comply with laws and regulations. However, if measures are too strict, this leads to an increased risk due to circumvention and shadow IT. Business rules help you find this balance. To guide you towards optimal use, here are best practices based on the experience of thousands of organizations.
Use up to 2 to 3 rules for broad categories of sensitive information
It is tempting to enable many rules to get the best possible protection. However, recognizing sensitive information is not an exact science. Every rule occasionally gives unwarranted notifications. This is especially true for rules that detect broad categories of sensitive information.
An SSN is clearly defined and therefore easy to identify. Sensitive medical, legal, or financial information is not. If you enable many of these rules, at least one rule will trigger a notification for many emails. This leads to notification fatigue and increases the risk that a notification is ignored when it is really justified. Therefore, we recommend using a maximum of 2-3 of these business rules.
Use safety level Suggestion for most rules
For the same reasons, it is important to limit the number of rules on safety level Warning or Error. Unnecessary warnings disrupt work and are frustrating. A suggestion is often sufficient for employees to make a conscious choice about safety.
Specifically, we recommend using:
- Error only for clearly identifiable information (for example, SSN) in the subject, where you will never get a false positive.
- Warning only for:
- Clearly recognizable sensitive information in the mail text (SSN, IBAN, and others.)
- Personal information
- Recommendation of BCC
- Suggestion for all other rules, such as medical or legal information.
Warn only for external recipients
For many organizations, internal mail traffic is already sufficiently secure. In that case, you can set business rules to go off only for external recipients. This ensures protection when it matters, with minimal disruption to employees.
Evaluate your policy with Zivver Insights
The key to good policy is to evaluate and adjust the policy. In your administrative environment, you can use Zivver Insights to get a better view of the operation of your business rules. With this, you can strengthen your policy and specifically increase awareness among employees.
Work with your Customer Success Manager
Implementing effective secure communication policies is no easy task. Your Customer Success Manager has already helped many similar organizations with this. We are happy to help you make the best use of business rules so that you communicate securely with minimal friction.
Guarantee of privacy and security
The business rules determine the appropriate security based on the content and recipients of messages and attachments. This means that they have to scan the contents of a message. This is often extremely sensitive information. Zivver takes all possible measures to process this information in a secure and privacy-proof manner. In this section we describe these measures.
The message and attachments are scanned by sending the content to Zivver servers over an encrypted connection. Here it is determined whether there is information that is sensitive according to your policy. During this scan, the server keeps the data in memory as short as possible (less than 1 second). After the scan, the server sends back the notifications through an encrypted connection. The notifications contain only the classification and never the sensitive data itself. After the scan, the content is entirely deleted from the server.
Only messages actually sent using Zivver are stored. Stored messages are encrypted with best-practice asymmetric encryption whereby only the sender and recipients can decrypt the message. Read more in Zivver’s Security by Design Whitepaper.
The implementation and effectiveness of these measures are reviewed annually by various independent auditors in ISO27001 and SOC2 audits and with technical pen tests. In addition, an independent data protection officer oversees processing at Zivver. You can find the certifications in our page Security Certifications.
If you have questions about how Zivver ensures privacy and security, you can find more information in our page Legal & Security. You can also discuss your questions with your Customer Success Manager.
Disclaimer
Business rules are an auxiliary tool and errors may occur in the application of business rules. Zivver aims to keep the frequency of errors as low as possible, but gives no warranties or guarantees in relation to the application of business rules and their accuracy.
Closing
The business rules help you prevent data leaks and comply with laws and regulations with minimal extra effort for your employees. To make optimal use of Zivver, it is important to set up the business rules properly. In this document you find all the information you need.
If you have additional questions, speak to your Customer Success Manager.
